Discover the power of proactive cybersecurity
FREE 2-Week CloudProtect Service
Book Now for Your Free Cyber Risk Health Check
Secure Your Digital Business with a Virtual CISO from In2net vCISO
Are you using Office 365 or Google Workspace for your business? If so, you need more than just basic security measures. At In2net vCISO, we provide you with a dedicated Virtual CISO (Chief Information Security Officer) who monitors and protects your digital assets in the cloud, ensuring your business stays secure against evolving cyber threats.
Why Choose a Virtual CISO?
A Virtual CISO offers continuous oversight and strategic security planning tailored to your organisation’s needs. With our expert team, you gain:
- 24/7 Monitoring: Round-the-clock surveillance of your digital environment to detect and respond to threats promptly.
- Tailored Security Strategies: Customised security plans designed to address the unique risks associated with your cloud services.
- Proactive Risk Management: Identifying and mitigating vulnerabilities before they can be exploited by cybercriminals.
Get Started with Your Complimentary Cyber Risk Health Check
Take the first step towards enhanced security by claiming your free Cyber Risk Enhancement Report. Simply click the button below to book a free consultation or sign up for your complimentary report. Our cyber security experts will analyse your organisation’s digital footprint and provide you with invaluable insights into potential cyber risks and vulnerabilities.
Don’t leave your digital business unprotected. With In2net vCISO, you have a Virtual CISO dedicated to safeguarding your cloud environment. Act now to secure your business today.
About us
Welcome to In2net vCISO: Your Trusted Cybersecurity Partner
At In2net vCISO, we are dedicated to providing comprehensive cybersecurity services tailored to meet the evolving needs of businesses in today’s digital age. With a relentless focus on safeguarding your organization’s digital assets and preserving your peace of mind, we offer a diverse range of cutting-edge cybersecurity solutions to address a myriad of threats and challenges.
At In2net vCISO, we are committed to empowering your organization with the cybersecurity solutions and support needed to thrive in today’s digital landscape. With our comprehensive suite of services and unwavering dedication to excellence, you can trust us to be your trusted cybersecurity partner every step of the way. Contact us today to learn more about how we can help safeguard your business from cyber threats.

Cybercrime Index
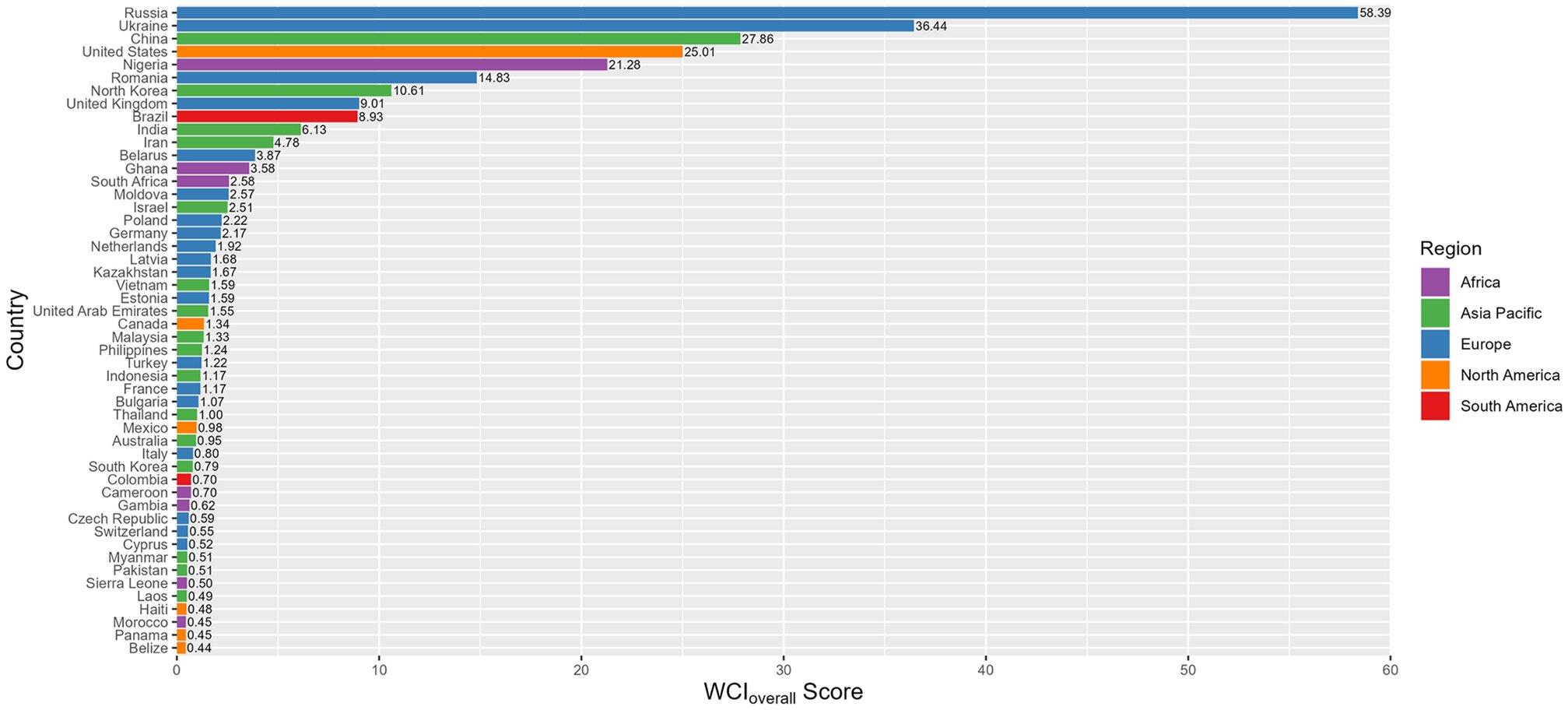
The Index above, published in the journal PLOS ONE, shows that a relatively small number of countries house the greatest cybercriminal threat. Russia tops the list, followed by Ukraine, China, the U.S., Nigeria, and Romania. The UK comes in at number eight.
Services

AI Development: Cutting-Edge Solutions for Your Business
Harnessing AI for Cybersecurity Enhancement
Threat Detection and Analysis
AI-powered algorithms can analyze vast amounts of data in real-time to detect patterns indicative of cyber threats.
Automated Response and Remediation
AI-driven automation streamlines incident response processes by executing predefined actions to contain security incidents.
Behavioral Analysis and User Authentication
AI algorithms can analyze user behavior patterns to establish and identify deviations that may indicate unauthorized access .
How AI Automation Works in Cybersecurity
AI automation in cybersecurity involves the use of artificial intelligence and machine learning algorithms to automate various security tasks and processes. These tasks may include threat detection, incident response, vulnerability management, and security orchestration. By analyzing vast amounts of data in real-time, AI algorithms can identify patterns, anomalies, and potential security threats that may go unnoticed by traditional security solutions. AI automation also enables organizations to respond to security incidents rapidly and effectively, minimizing the impact of cyber attacks and reducing the workload on security teams.
AI automation is transforming the cybersecurity landscape, empowering organizations of all sizes to detect, respond to, and mitigate cyber threats with unprecedented speed and efficiency. Whether it’s large enterprises, SMBs, MSSPs, government agencies, or SOCs, a diverse range of organizations are harnessing the power of AI automation to enhance their security defenses and stay one step ahead of cyber adversaries in today’s dynamic threat landscape.

Phishing emails are sent
every day
Data breaches occur as a
result of phishing attacks
of users cannot identify a
sophisticated phishing email
of UK businesses reported a cyber-attack in 2020
Threat Detection and Analysis Services
In today’s digital landscape, the failure to invest in robust Threat Detection and Analysis services can have devastating consequences for organizations. Without proactive monitoring and analysis of security threats, businesses expose themselves to significant financial losses, reputational damage, and operational disruption. Let’s examine a real-life example to illustrate the potential cost and damage of neglecting Threat Detection and Analysis Services and explore how it could have been prevented.
Real-Life Example:
In 2017, Equifax, one of the largest consumer credit reporting agencies, experienced a massive data breach that exposed the personal information of over 147 million individuals. The breach occurred due to a failure to detect and patch a known vulnerability in Apache Struts, a popular open-source web application framework used by Equifax for its online services. Hackers exploited this vulnerability to gain unauthorized access to sensitive customer data, including names, Social Security numbers, birth dates, and addresses.
Major incidents since the introduction of GDPR
The General Data Protection Regulation
(GDPR) came into effect across the European Union.
The ICO fines British Airways and Marriott International for GDPR violations.
BA: £183.39 million - Marriott International: £99.2 million
The ICO fines Ticketmaster
The ICO issued a fine to Ticketmaster for failing to secure its online payment pages adequately: £1.25 million
39% of UK businesses reported suffering a cyber attack in 2022.
Cyber attacks globally increased by 125% in 2021 compared to 2020.

The Importance of Employee Cyber Awareness
In today’s digital age, organizations face an ever-growing array of cyber threats that can compromise sensitive data, disrupt operations, and damage reputations. While investing in robust technical solutions is crucial, it’s equally important to recognize the vital role that employees play in safeguarding against cyber attacks. This article delves into the significance of employee cyber awareness and highlights the benefits of prioritizing training and education in bolstering organizational cyber defenses.
According to a report by IBM Security, human error is a contributing factor in 95% of security breaches. This statistic underscores the critical need for organizations to focus on enhancing employee cyber awareness as part of their overall cybersecurity strategy. “Employees are often the weakest link in the cybersecurity chain,” says John Smith, CEO of In2Net Solutions. “Empowering them with the knowledge and skills to recognize and respond to cyber threats is essential in mitigating risks and protecting organizational assets.”
Safeguarding Your Digital Mobility
As mobile devices continue to proliferate and play an increasingly central role in our personal and professional lives, prioritizing Mobile Device Security is paramount. By implementing robust security measures, organizations and individuals can protect sensitive data, mitigate cybersecurity risks, and ensure the integrity and confidentiality of information processed and stored on mobile devices. Embracing Mobile Device Security as an integral component of cybersecurity strategies enables us to harness the benefits of mobile technology while safeguarding against the evolving threats of the digital age.
Remote & Mobile Device Security is indispensable in safeguarding organizations against the evolving threat landscape and ensuring the integrity, confidentiality, and availability of data accessed and processed through remote and mobile devices. By implementing robust security measures, adhering to best practices, and fostering a culture of security awareness, organizations can mitigate risks and protect their digital assets in an increasingly mobile world.

Vulnerability Assessment
Comprehensive Scanning: Our team conducts thorough assessments of your network, applications, and systems using industry-leading scanning tools and techniques to identify vulnerabilities, misconfigurations, and potential entry points for attackers.
Risk Prioritization: We prioritize identified vulnerabilities based on severity, impact, and exploitability, allowing you to focus your resources on addressing the most critical risks that pose the greatest threat to your organization.
Detailed Reporting: Our Vulnerability Assessment reports provide clear, actionable insights into identified vulnerabilities, including recommendations for remediation and mitigation strategies tailored to your organization’s specific needs and priorities.
Ongoing Monitoring: We offer continuous monitoring services to ensure that your organization remains protected against newly discovered vulnerabilities and emerging cyber threats, providing peace of mind that your security posture is regularly assessed and updated.
Cloud Security Services
Enhanced Data Protection: Our CloudProtect Services help protect your sensitive data and assets in the cloud, reducing the risk of data breaches, unauthorized access, and data loss.
Improved Compliance: By addressing security risks and compliance gaps in your cloud environment, we help you meet regulatory requirements and industry standards, ensuring the security and privacy of your data.
Reduced Security Complexity: We streamline cloud security management by providing centralized visibility and control over your cloud resources, simplifying security operations and reducing the complexity of managing multiple cloud environments.
Cost Savings: Investing in Cloud Security Services can result in cost savings by mitigating the financial impact of security incidents, data breaches, and regulatory fines, as well as reducing the overhead associated with managing security infrastructure and resources in-house.
Peace of Mind: With In2net vCISO as your trusted partner, you can have peace of mind knowing that your cloud environment is secure, resilient, and protected against evolving cyber threats.


What is Ransomware?
Ransomware is a type of malware designed to deny access to a computer system or files until a ransom is paid. It typically infiltrates a system through phishing emails, malicious attachments, or exploiting vulnerabilities in software. Once inside, it encrypts files, making them inaccessible to the user. The attackers then demand payment, usually in cryptocurrency, in exchange for the decryption key.
How Ransomware is Used
Ransomware attacks can have devastating consequences for individuals and businesses. Attackers often target organizations with valuable data, such as financial institutions, healthcare providers, and government agencies. They exploit vulnerabilities in systems and use social engineering tactics to trick users into opening malicious files or clicking on malicious links. Once the ransomware is activated, it spreads rapidly throughout the network, encrypting files and causing widespread damage.
Cyber Risk Health Check
Threat Detection and Analysis Services
At In2net vCISO, we offer cutting-edge Threat Detection and Analysis services to safeguard your organization against cyber threats. Our comprehensive approach combines advanced technologies and expert analysis to proactively identify, analyze, and respond to security incidents, helping you stay one step ahead of cyber adversaries.
Simply click the button below to Book a free Consultation, or sign up for your complimentary Cyber Risk Health Check.

Stay connected with us through our social media channels and newsletter to receive the latest updates, cybersecurity tips, and industry insights straight to your inbox.
Website created By In2net Solutions © 2024. All rights reserved